Golden Keylogger v2.00 Keyloggers get a lot of bad rap because they spy on people. But this keylogger is a good one. In fact, Golden Keylogger is Net's only family-friendly keylogger. What gives us the right to make this claim? Because the only reason Golden Keylogger was created in to protect you and your family, not to spy on people.
- Golden Eye 4.50 (keylogger) Free
- Golden Eye 4.50 (keylogger) Price
- Goldeneye 4.50
- Goldeneye 4.50 Download
- Golden Eye 4.50 (keylogger) Pro
- Very easy to use. Try Now Buy Now ( Only US $29.95) Recent Awards. Golden Eye was rated with highest 5 stars at spy software catalog of 5Star-Shareware, The UK's Premier Website for Shareware and Freeware Downloads. Golden Eye received the highest possible 5 Stars and the 'Editor's Pick' at WebAttack's internet spyware catalog the world's.
- Golden Eye 4.50 Spy all activity on your computer. Family Key Logger 4.24 An invisible keystroke logger. Know what others are doing on your computer while you are.
Golden Eye Review
A keylogger with a bit misbalanced set of functions and an outdated interface. Despite the lack of some functions can be used for employee monitoring and monitoring of your home PC. Doesn't support Windows 7, so should be used on Vista, XP or 2000.In our testing, it gets 384 out of possible 1172 points.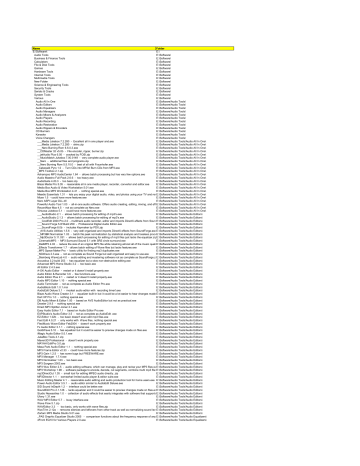
Golden Eye 4.50 (keylogger) Free
Advantages:- Grouping of the intercepted information into categories
- Good file-activity monitoring
- Both sides interception in 3 of 5 messengers
- Good visual surveillance
Disadvantages:
- Weak URL interception
- Not enough stealthiness level
- Low filtration
- No e-mail monitoring
Today we are reviewing Golden Eye monitoring software.
To install the program you need to pass through 5 screens among which you need to read and accept EULA, specify the installation folder, decide whether you want setup to create an icon of the program on your desktop or not, and to confirm your choice. We do all this, and once the installation process is finished, we leave 'Launch Golden Eye' item marked and click 'Finish' button.
The main window of the program has 5 sections, namely: General, Report, Monitoring, Options and About. 'General' section allows a user to choose between Invisible and Normal modes and has information about such buttons as: 'Start Monitoring', 'Stop' and 'Hide'. Intercepted information, listed in 'Report' section is grouped into categories. This feature, in addition to such tools as 'Search', 'Replay Screenshots' and 'Delete Selected Records' buttons makes log-viewing really convenient. 'Monitoring' section allows user to configure screenshots', web-sites', chats' and other monitoring capabilities, while the 'Options' section lets a user to configure 'general' program behavior, such as enable or disable password protection, assign a hotkey, specify the folder for log-files' saving, etc. The last section in the list ('About') contains information about the keylogger, its vendor and has the 'Uninstall' button. 'Start monitoring', 'Stop' and 'Hide' buttons are located below the main screen and can be accessed from any of the sections.
The main advantages of the program are good file-activity monitoring (4 of 5 main file-activity operations are logged), not bad chat conversations interception (3 of 5) and good visual surveillance options.
Unfortunately, the program has disadvantages that are, unfortunately, very substantial: keylogger intercepts only URLs visited in IE, does not log e-mails sent and received, has very weak filtration options, no parental control tools and only one method of remote log-files' delivery — by LAN. The stealthiness level of the product is also below the middle, as it is really easy to find its directory.
Summing up we can say that despite the program's substantial disadvantages it will come in handy for all the groups of users as its functions are enough to monitor users in almost all the range of its computer activities.
Monitoring Software Features
Monitoringthis group analyzes what monitoring functions the products has, such as keystroke, clipboard, file-activity, etc monitoring.

Golden Eye 4.50 (keylogger) Price
Goldeneye 4.50
Online Monitoringthe group that reflects the availability of the functions to monitor users’ online activity, such as URLs visited, 2-side chat conversations interception and emails sent/received.
Securitythis group shows how hidden the product is and what self-protection mechanisms it has.
Reportsthe group that basically analyzes the convenience of the intercepted information reading, including not only the ways to filter and show it, but also to deliver it remotely.
Otherother functions that cannot be part of any of the other groups listed, though a still very important such as parental control functions, languages, reactions to specific keywords, etc.

Goldeneye 4.50 Download
OS Supportthis group reflect the number and quality of the operation systems supported by the products.
Golden Eye 4.50 (keylogger) Pro

Users’ reviews and comments for Golden Eye
Golden Eye currently has no reviews. Be the first to review it!

Add your review
Your Name:Your E-mail:
Rate this product:
Title:50 characters max
Pros:10 to 1000 characters
Cons:10 to 1000 characters
Summary (optional):5000 characters max
Verification code: