Elcomsoft Phone Breaker 9.60.36843 Key here It is enables forensic access to password-protected backups for smartphones and portab. Windows Password Breaker Professional 5.2 Serial Key. Windows Password Breaker Professional 5.2.0.0 Setup+Crack.zip (4.91 MB) Select download membership type SLOW DOWNLOAD Wait sec. Windows 8 pro serial key. Windows Password Breaker Windows 7. Windows Password Breaker Download. Portable Elcomsoft Phone Breaker Forensic Edition 9.05.31064 Forensics Tools Mobile Utilities Perform logical and over-the-air acquisition of iOS, Windows Phone 8/8.1, Windows 10 Mobile and BlackBerry 10 devices, break into encrypted backups, obtain and analyze information from Apple iCloud.
Q: Will your product jailbreak my iPhone, unlock it from the carrier, remove passcode lock, or reset a SIM card PIN code?
A: Sorry, no way.
Q: So, what is it all about?
A: Phone Password Breaker takes care of password-protected iPhone, iPod Touch and iPad backups.
Q: I don't create backups of my iPhone and don't even know how to do that, why should I care?
A: In fact, iTunes creates a backup every time you sync your device with a computer. Now, it is arguable whether doing that automatically without user intervention is a good idea, but like it or not, you end up having backups on your computer. (You still have the ability to create a backup manually at any time, of course).
Q: Where are these backups stored?
A: By default, backups are stored in the following folders:
- Mac: ~/Library/Application Support/MobileSync/Backup/
- Windows XP: Documents and Settings(username)Application DataApple ComputerMobileSyncBackup
- Windows Vista and Windows 7: Users(username)AppDataRoamingApple ComputerMobileSyncBackup
Q: You're right, the backups are there, but what's inside? I can see several folders there, with long weird names, and thousands of files inside with similar names and .mdinfo or .mddata extensions. Only three files have friendly names, and look like XML.
A: To say the least, backups contain almost everything from your iPhone (except iTunes library), and definitely all your private information. According to the article in Apple Knowledge Base, the following information in particular is there:
- Address Book and Address Book favorites
- App Store Application data
- Application settings, preferences, and data
- Autofill for webpages
- CalDAV and subscribed calendar accounts
- Calendar accounts
- Calendar events
- Call history
- Camera Roll
- In-app purchases
- Keychain
- List of External Sync Sources (Mobile Me, Exchange ActiveSync)
- Location service preferences for apps and websites you have allowed to use your location
- Mail accounts
- Managed Configurations/Profiles
- Map bookmarks, recent searches, and the current location displayed in Maps
- Microsoft Exchange account configurations
- Network settings (saved wifi spots, VPN settings, network preferences)
- Nike + iPod saved workouts and settings
- Notes
- Offline web application cache/database
- Paired Bluetooth devices (which can only be used if restored to the same phone that did the backup)
- Safari bookmarks, cookies, history, offline data, and currently open pages
- Saved suggestion corrections (these are saved automatically as you reject suggested corrections)
- SMS and MMS (pictures and video) messages
- Trusted hosts that have certificates that cannot be verified
- Voice memos
- Voicemail token
- Wallpapers
- Web clips
- YouTube bookmarks and history
Why all that stuff is stored in separate files instead of the single archive, and what is the idea behind the file names remains with Apple. Our guess, the file names are just hash sums of full paths to this file when stored inside the device, but we have not checked. Does that really matter?
Although the files don't look readable, they are not encrypted. In fact, they are just ordinary binaries in SQLite database format. If you don't know what that is, never mind; it does not really matter. What is important, most of your private information is stored on your computer in plain, unprotected form.
Q: It seems to be a good idea to create iPhone backups, right?
A: Absolutely.
Q: If all that information is already there, can I transfer it all to a new device by simply restoring the backup to a new device (other/newer model)?
A: Yes, but some restrictions apply. Keep reading, you'll be surprised.
Q: What about backup passwords?
A: It's time to quote Apple again:
«In the iTunes Summary screen, select 'Encrypt iPhone backup' if you want to encrypt the information stored on your computer when iTunes makes a backup. Encrypted backups are indicated by a padlock icon (as visible below in the Deleting a Backup section), and a password is required to restore the information to iPhone. You may want to write down the password for your backup and store it in a safe place. If you use a Mac, when you set a password you can select to store the password in the keychain. With iOS 4 and later, you can transfer your keychain backup to a new device if you encrypt the backup.
Warning: If you encrypt an iPhone backup in iTunes and then forget your password, you will not be able to restore from backup and your data will be unrecoverable. If you forget the password you can continue to do backups and use the device, however you will not be able to restore the encrypted backup to any device without the password. You do not need to enter the password for your backup each time you back up or sync.
If you cannot remember the password and want to start again, you will have to do a full software restore and when prompted by iTunes to select the backup to restore from, choose Set up as a new device.»
Try reading the above text carefully until you get it. If you’re like most of us and just don’t get it after several tries, bear with us.
Q: If I ever decide to set a password and forget it later, should I be able to set another one rather easily? I mean, I don't need old backups at all. Or can I just connect my iPhone to another computer and create another backup with my new password or without a password at all?
A: Sorry, no way. If you ever set an option to encrypt your backups with a password, your choice will be stored deep inside your iPhone. Moreover, the entire password verification is also performed by the iPhone, deep inside the iOS kernel and not by iTunes as you may guess.
Q: Really?
A: Yes, no kidding.
Q: Then, what am I going to do if I forget the password?
A: R.I.P. to your iPhone! :)
Seriously, there are only two realistic solutions. First, you can follow Apple's recommendation to perform a complete reset of your phone, setting up your device as a new one and losing all iPhone content, from contacts to photos (see above). It’s like pulling a tooth: you lose it, but hey – it’s free!
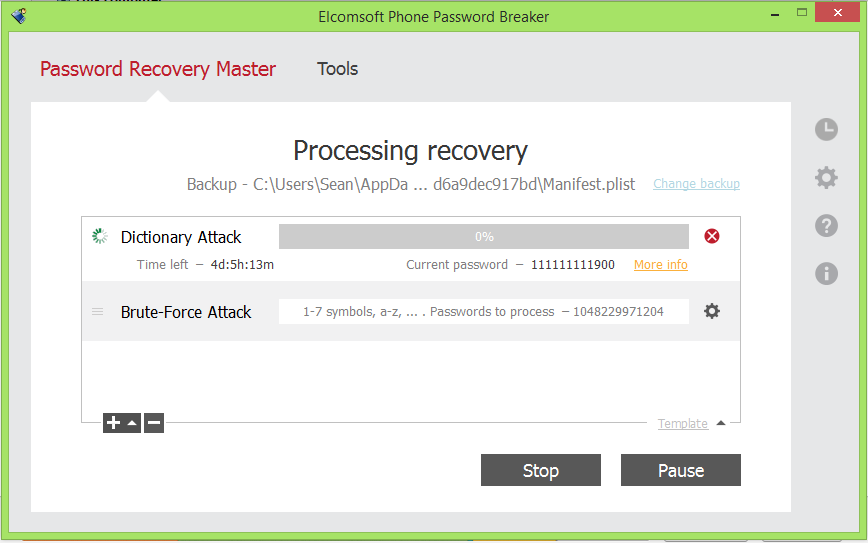
Your second option is using our Phone Password Breaker. It’s about time to mention our own product in this FAQ!
Q: So how your product can help?
Elcomsoft Phone Breaker 9.05 Registration Code Download
A: First, the legal disclaimer: we give no guarantees. Our tool only gives you a chance. It’s a good fat chance, but no snake oil or a 100% guarantee.
The iPhone backup encryption is good enough. Well, it is near perfect by our standards. That’s to say, it’s really secure. The password can be recovered only with time-consuming brute force and dictionary attacks, just like with ZIP, RAR, Microsoft Office and other tools featuring good encryption. Our products will *try* to recover your password, but success rate heavily depends on your creativity: the shorter and easier your password was, the better your chances are. Only relatively short and simple passwords can be recovered in a reasonable time.
Q: What do you mean by 'time consuming' and 'reasonable time'?
A: A lifetime? Seriously, with protection as good as that, it may take centuries to recover a long password. The factors that affect the time (and your chances) are:
- The speed of your computer, both CPU and graphics card (to be explained later)
- The length and complexity of your password
- Any information you supply about your password (including your password-related habits)
- Your patience.
Q: Can you elaborate?
A: CPU speed is self-explanatory. As for the length and complexity, it's very simple: the program will have to try all possible combinations to guess your password. For example, if your password contains small letters only, the number of combinations to try increases 26 times with each extra letter. If your password contains numbers and both small and capital letters, it's a bit more complex mathematics behind. In a word, the total number of combinations is a (number of different characters the password may contain) in a power of (password length). For example, there are 62^6 = 56,800,235,584 (56+ billion) possible 6-character alphanumeric passwords. And if you don't have any info about the password and just know the length and the fact that it is alphanumeric, the program must try them all until it finds the one that matches.
As to the habits, do you know how you usually select a password? Some people calling themselves 'smart' just create complex random ones, usually with special software. Bad choice. You can remember a few of those, but definitely not all; you will have to write them down eventually (say bye-bye to security!), or keep them in a special program or database (can you trust it? Is it really secure? How do you know? And do you have a backup of that database?)
Anyway, we're not going to discuss with approach is the best (we have a separate whitepaper on that), but if your password is NOT totally random, then most probably it contains a commonly used word, or a phone number, or your pet name, or a football team, or just 'god', 'sex' or 'topsecret'. No way? It’s probably 'Paris Hilton' then. If you already tried all those but failed to guess the right one, then you definitely need Phone Password Breaker. It already includes a 'wordlist' with most commonly used passwords in English, German and Russian languages, with extra lists available from the Internet. There are special options in the product allowing to check variations of the words from the wordlist; we call them 'smart mutations'. Read product docs for more info.
Finally, you’ll need patience. If you're lucky, your password might be recovered in seconds; if not, it may take just a bit longer. Like, years or centuries.
Q: How do I get better speed?
A: We’re not going to be an excuse for buying a new PC. However, here’s a perfect chance to upgrade your video card. For recovering your passwords, the speed of your graphics card is much more important than the speed of the CPU. Phone Password Breaker offloads complex calculations onto the video card, and, surprisingly, you get much better performance (especially if you are a hardcore gamer). Latest AMD and NVIDIA boards do wonders, speeding up password recovery some 10 to 50 times compared to CPU only. For more information, read GPU acceleration FAQ.
Q: Back to iPhone backup, can I restore it onto a different device?
A: Yes you can. However, there’s one thing stored in the backup: 'Keychain'. There's just something special about it.
Q: What is a keychain?
A: Keychain is a 'storage' that includes email account passwords, Wi-Fi passwords, and passwords you enter into websites and some other applications.
Elcomsoft Phone Breaker 9.05 Registration Code
Q: So what?
A: Apple's turn:
«If you encrypt the backup with iOS 4 and later, the keychain information is transferred to the new device. With an unencrypted backup, the keychain can only be restored to the same iPhone or iPod touch. If you are restoring to a new device with an unencrypted backup, you will need to enter these passwords again.»
Q: How the keychain is encrypted?
A: Presuming you know at least something about encryption, speaking of iOS 4+ only, here is the situation:
If a backup IS NOT password-protected, the keychain is encrypted using 'hardware' keys stored in the iPhone and not accessible from the outside. You can safely restore such backups to the same iPhone; however, if you restore it to another iPhone, the keychain will be lost completely.
If a backup IS password-protected, the keychain is encrypted using software keys that are generated from the backup password. As a result, you can restore such backups to any device, and keychain information will be restored as well. In order to restore the backup, you will have to enter the original password, so you must know it. Or you can crack it with Phone Password Breaker.
Q: What is the reason behind this strange behaviour?
A: Officially, security. Or privacy. Or some other nice marketing word. We'd vote for usability though.
Q: Can I view the contents of the keychain?
A: Yes, that's what we added to the latest version of Phone Password Breaker. Select 'Keychain Explorer' from the 'File' menu, choose a backup from the list of available (encrypted!) ones, enter your backup password when prompted, and see what happens.
Q: What if I only have a backup without the password set on it?
A: Create a new backup with the password. It's easy!
Q: There are a lot of items in the keychain, but how do I understand them?
A: We tried giving 'friendly' names to all fields; there is also an explanation that appears in the small window when you highlight a field. In most cases, logins are stored under the 'Account' field, and passwords under the 'Data' field. There is also information specific to some keychain items such as mail accounts, including server addresses, port numbers, protocols, etc.
Elcomsoft Phone Breaker 9.05 Registration Code List
Q: For some items, there is no password but some data that looks like encryption keys. What are they for?
A: Keychains are system-wide storage. They aren’t restricted to Apple software only. Any iOS compliant application can store any information in the keychain, thus only its developers know exactly how to interpret that data. We just can't check all applications from AppStore to see what they store in the keychain.
Q: Can I extract other useful information from the backup such as date/time when I connected to a specific wireless access point?
A: The possibility is there, just not with our software. We only help recovering backup passwords and allow browsing the keychain. If you need advanced access to backup information, we recommend using software such as Oxygen Forensic Suite. Here is some other software that works with iTunes backup:
- iBackupBot (Windows and Mac OS X)
- iPhone Analyzer (Windows)
- iOS Backup Analyzer (Windows)
- iExplorer (Windows and Mac OS X)
- iPhone / iPod Touch Backup Extractor (Mac OS X)
- PhoneView (Mac OS X)
Elcomsoft Phone Breaker 9.05 Registration Code Free
Q: There's a lot of interesting information in the keychain! I want to perform a thorough analysis; how do I do that?
A: Use Phone Password Breaker to export it into an XML or plain-text file. XML is a universal format that can be used in many ways. We did our job, now it’s your turn.
Q: Is all that legal?
Elcomsoft Phone Breaker 9.05 Registration Code Generator
A: Absolutely. If it’s your iPhone and your backups, or if you have a permission from the owner, or there’s a court order, or you know for sure the owner wouldn’t mind, or suspect the owner of cheating… ;-)
Q: Thanks for your explanations! Anything else I need to know about passwords, backups, iPhone, Apple or computers in general?
A: You're welcome! Just keep reading our news, and we’ll keep you updated.